Let us say you are creating an application on Azure using Azure App Service because of course, you don't want to manage and patch virtual machines. You found out that you need to store some environment variables so your application can read it and connect to a database running somewhere. You also want to ensure that these environment variables are secured, so no unauthorized party can access these sensitive pieces of information.
How do you achieve this? Well, let us check out Azure Key Vault reference for Azure App Service. When we are finished with this guide, you will be able to explain the how and why of Azure Key Vault reference.
The Challenge
Let us look at the challenge more closely before diving into the solution. Azure App Service is a HTTP-based service for hosting web applications, APIs, and mobile backends. Most HTTP-based hosting services allow you to define environment variables, which you can then access from your application during runtime.
Azure App Service is no different, in that it allows you to define environment variables that your application may need to read later on. By default, you can define these variables in plain text, so anyone who has access to your App Service can potentially read its values. Think about the consultant you hired to help with a new feature, reading your database username and password that you put in Azure App Service. This must be a nightmare, right?
The Solution
Now, how do we "encrypt" these variables, to prevent unauthorized access whether intentionally or unintentionally? Azure Key Vault! Azure Key Vault is a key management service that securely stores secrets and keys for your applications to consume later on. Think about your Twilio API keys, or application's secret key, or even your database access credentials. These are all sensitive pieces of data that you want to protect, but your application should be able to access whenever it needs in a seamless manner with no code change.
I have a sample FastAPI (it can be found in my GitHub repo ) app that needs to connect to a PostgreSQL database.
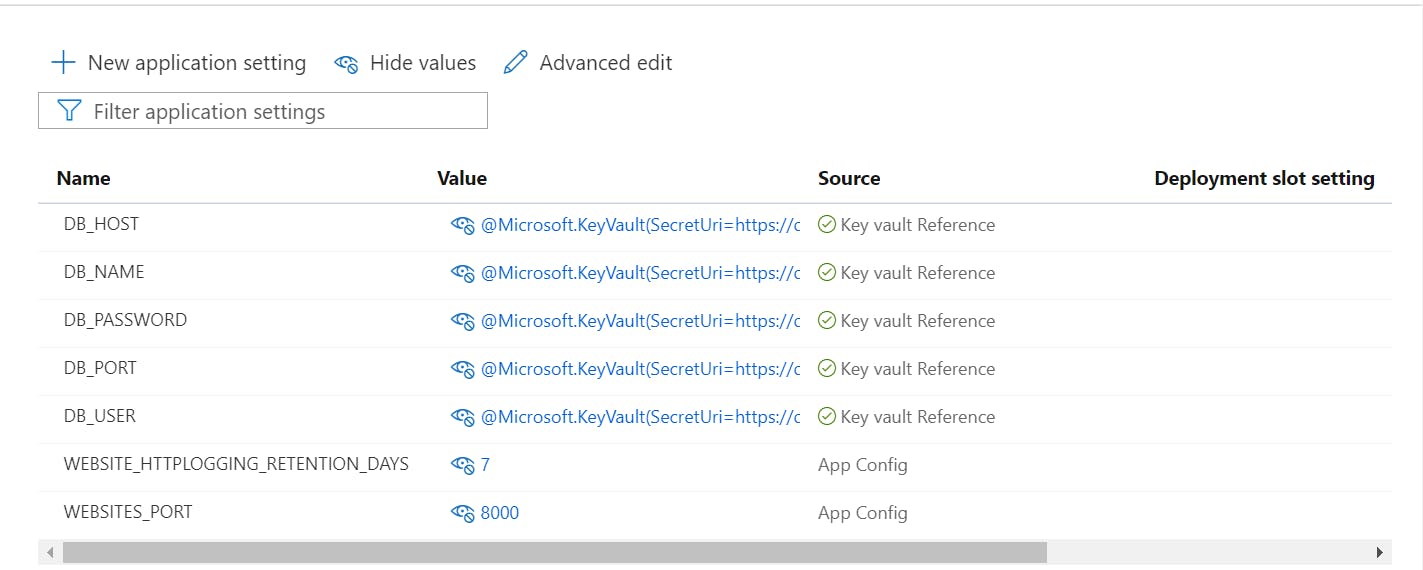
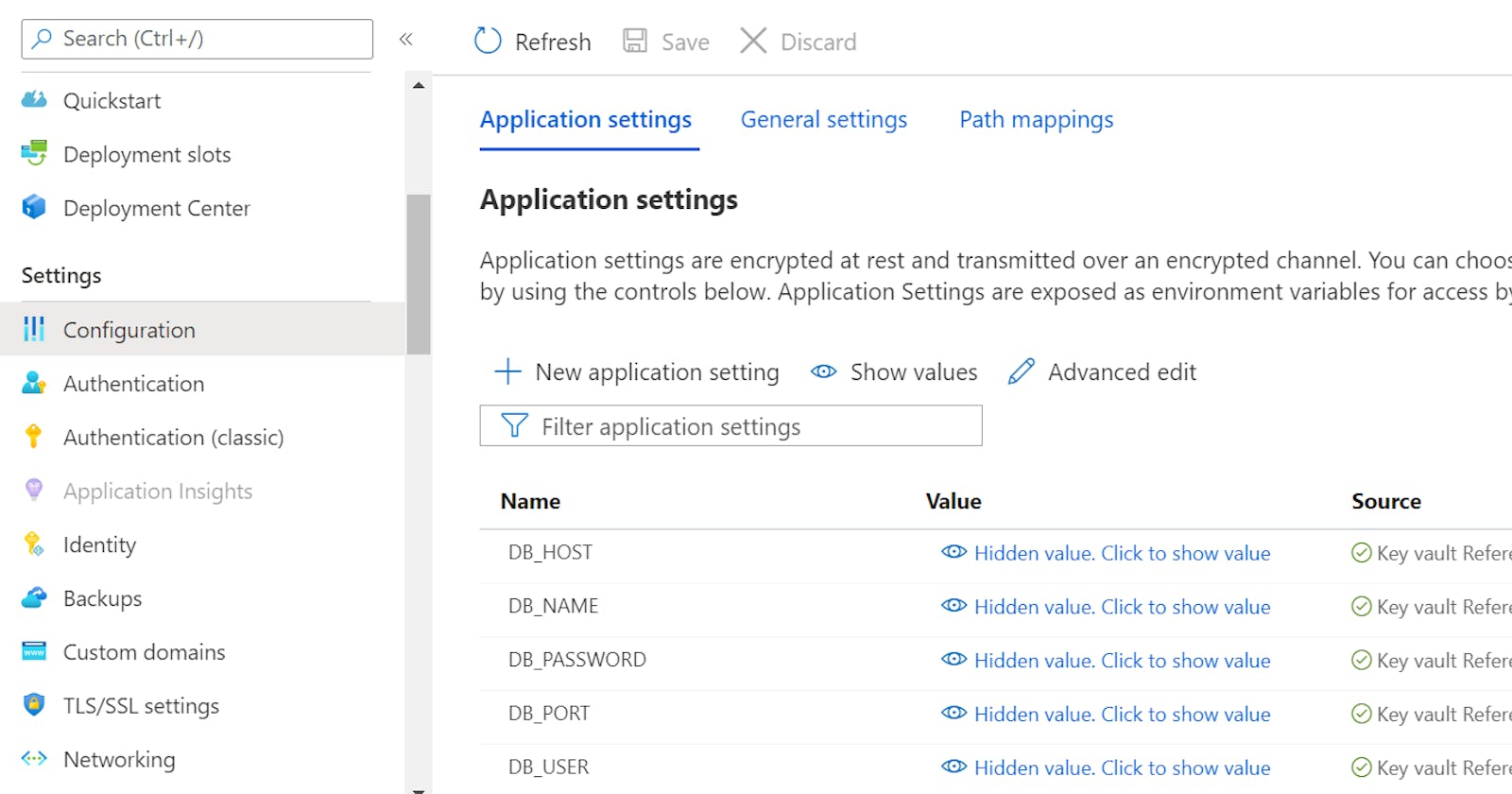
The screen capture above shows that all the database-related secrets are referenced in Azure Key Vault, while WEBSITES_PORT is stored in plain text and can be read and understood by anyone who has access to the App Service.
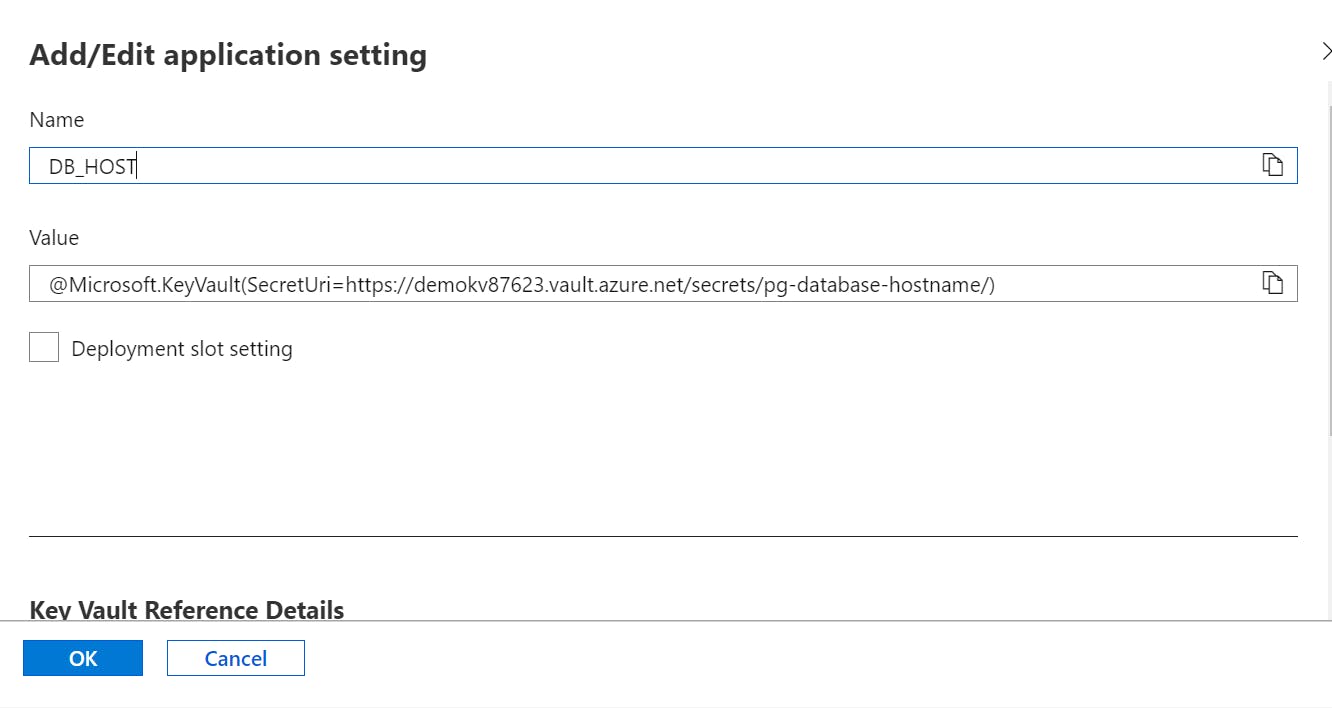
A closer look at the DB_HOST environment variable (or application setting as called by Azure App Service) confirms that the actual value is stored in Azure Key Vault, reducing the likelihood of unauthorized access.
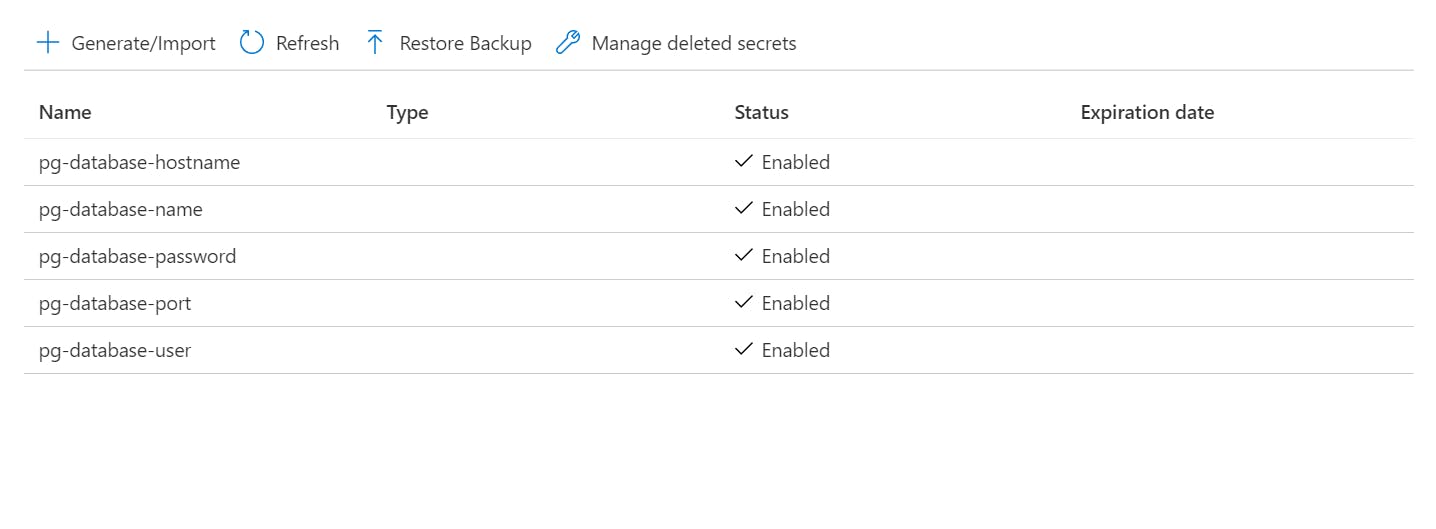
In the Azure Key Vault, we have all the secrets stored and we simply give Azure App Service access to List and Get the values, following the principle of least privilege.
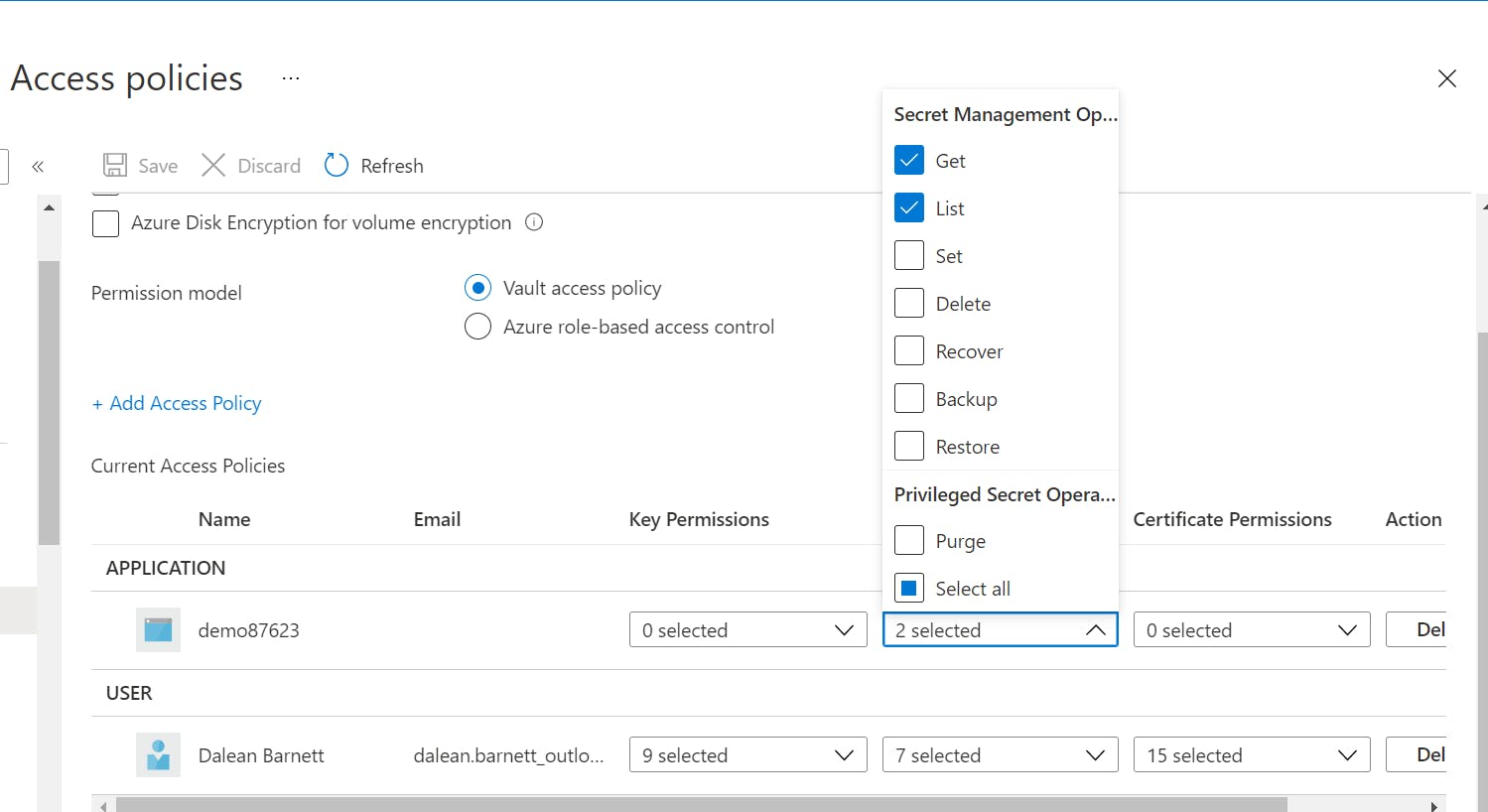
In the Azure Key Vault Access Policies blade, I assigned the Get, and List secrets permissions to the Azure App Service through its managed service identity. You will soon see that I did not have to write any special code to access the environment variables in my app.
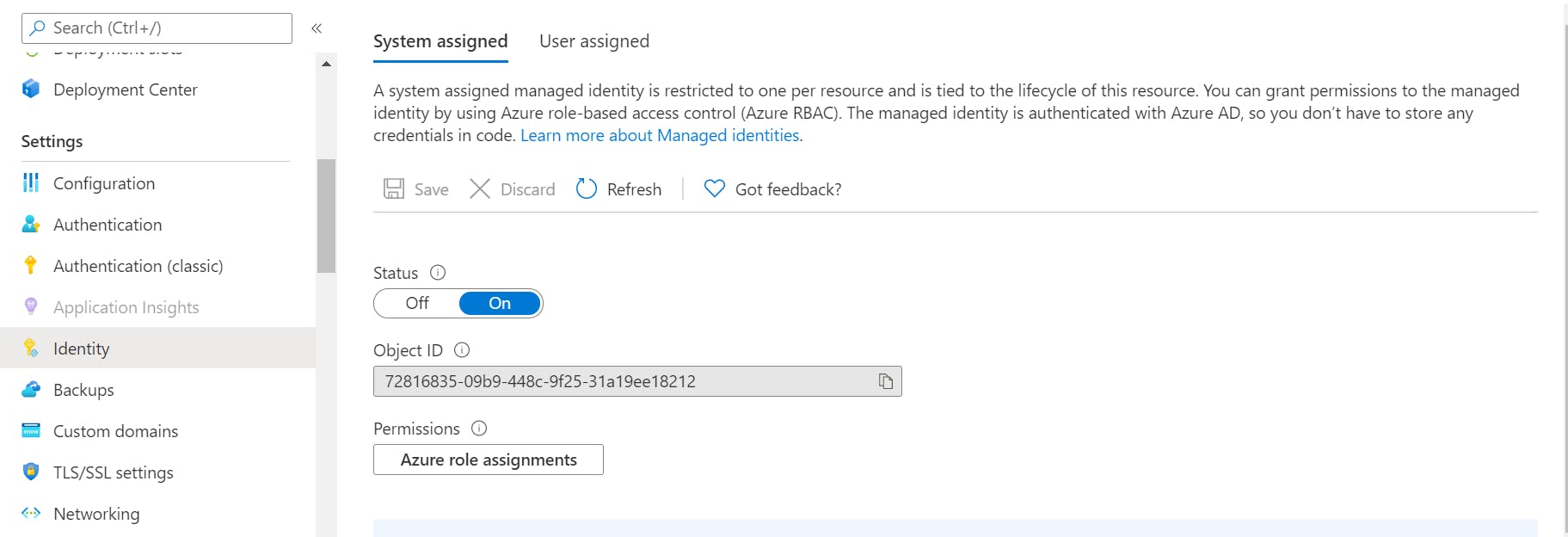
Here you can see that I enabled the System assigned managed identity from within the App Service's identity blade.
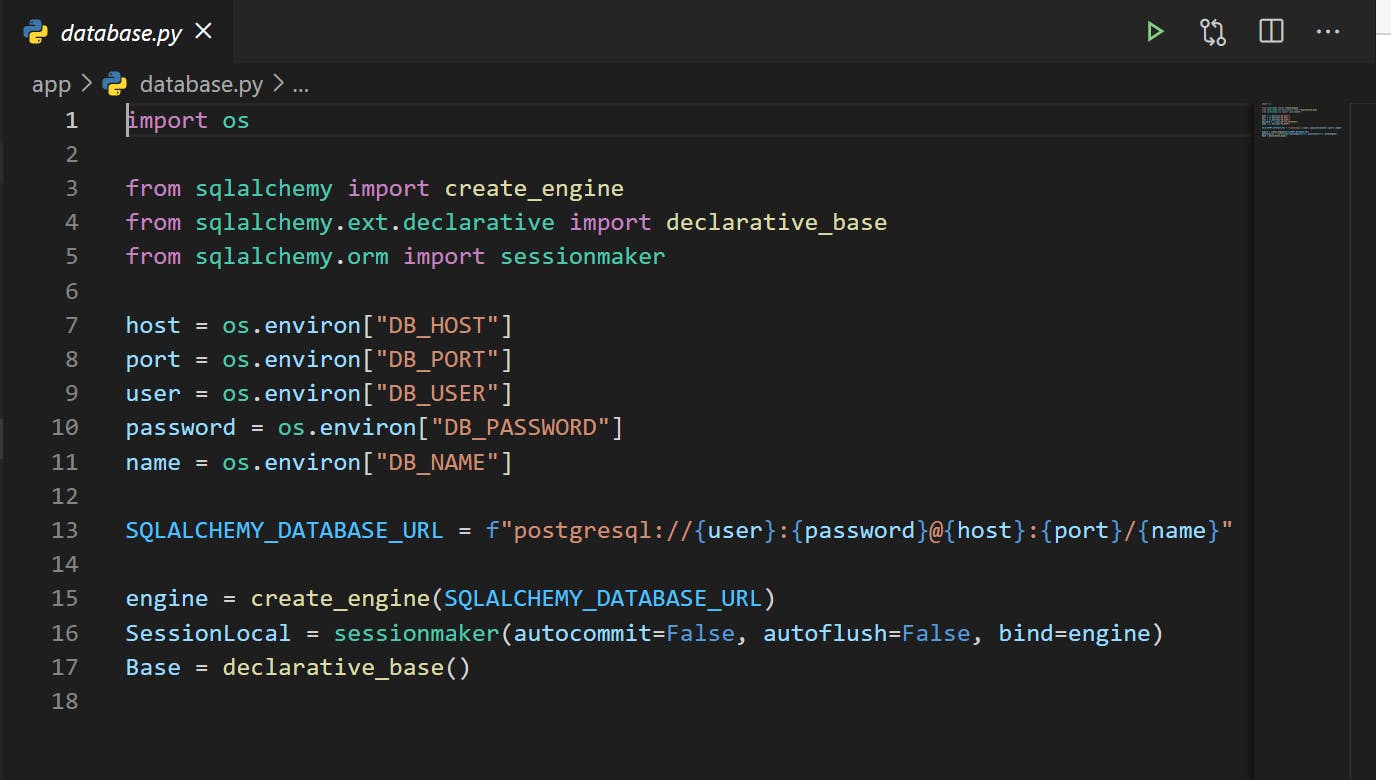
In my app you can see that I am accessing the environment variables through Python's default construct - os.environ["ENV_NAME"].
Let's call our app from Postman to see if it works
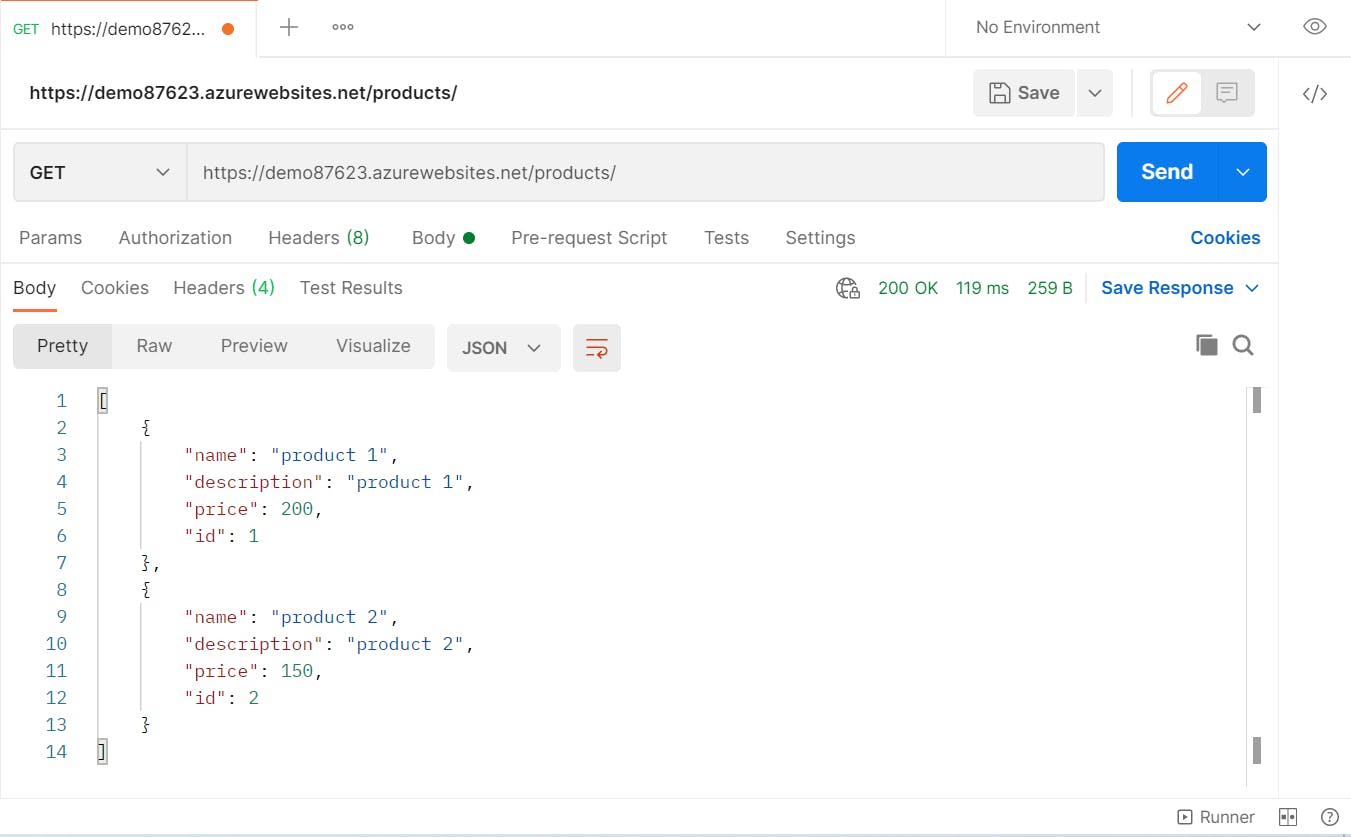
This is a GET request to the products endpoint https://demo87623.azurewebsites.net/products/ and we were able to connect to the database and retrieve a list of products.
Key Takeaway
As devs and ops, we need to ensure that our applications and platforms are secure to reduce the attack surface. Too often we overlook basic security controls and take for granted the number of security threats that exist. Azure App Service is a great platform for deploying our applications and while Microsoft does the patch management and infrastructure maintenance, We are still responsible for some aspects of the security in our application stack, like protecting our secrets and keys. Azure Key Vault helps us to get this done with zero code change.